How to Aid in Phishing Scam
Prevention
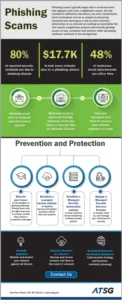
Phishing scams typically begin with a received email that appears sent from a legitimate source, but the method of infiltration and attack can take varied forms. Some techniques can be as simple as deceiving someone into clicking on a link to enter sensitive information or as intricate as running an executable file that spoofs a legitimate process and covertly gaining access to your computer and network while spreading malicious software in the background.
For more information on how you can protect your network and users against phishing scams and other cyberattacks, please download our latest infographic today.